Cybersecurity for Kansas City's Small & Medium Businesses
We believe every business deserves rock solid confidence in their cybersecurity no matter its size. For one clear monthly price you get enterprise grade protection and support from industry experts. Relax knowing we’ve got your back against digital threats. Fearless protection with zero fluff.

About SIXCYBER

Our Mission
Enterprise-grade cybersecurity for Kansas City SMBs via local experts.
SIXCYBER was founded to make world-class cybersecurity accessible to small and medium businesses. Bill Swearingen, our founder, is a trusted industry expert with over two decades of frontline experience. He’s built and led cyber defense teams for major enterprises and even crafted national strategies to defend against cyber warfare. Bill co-founded SecKC – the world’s largest monthly cybersecurity meetup – giving him a deep network of top local talent.
After seeing too many companies devastated by preventable breaches, he created SIXCYBER to bring nation-state-level security to SMBs. Our mission is simple: enterprise-grade cybersecurity for small and medium sized businesses via friendly local experts. We harness Bill’s unmatched expertise and our talent network to deliver big-company protection on a small-business budget. With SIXCYBER, you get a confident partner who speaks your language and genuinely cares about keeping your business safe.
Our process
Every business deserves a security partner that’s as hands-on and personal as it is capable. At SIXCYBER, our three-step process takes the guesswork out of cybersecurity - bringing you immediate defenses, expert oversight, and unwavering support. From a jargon-free onboarding to a mentor-driven team and 24/7 protection, we make sure your defenses evolve alongside your business, keeping you safe and focused on what you do best.
Personalized Onboarding
Getting started is easy and jargon-free. We begin with a quick security assessment of your IT environment and business needs, then deploy our full toolkit with minimal disruption to shore up defenses from day one.
Expert + Apprentice Team
Every client is paired with a veteran cybersecurity engineer and a local apprentice. Two sets of eyes on your security—top-tier protection, rapid response, and on-the-job mentorship to grow the area's next-generation of talent.
High End Protection
We use a carefully selected toolkit of enterprise-grade tools and services to cover every angle of your cybersecurity, all optimized for SMB needs.
Ongoing Support
SIXCYBER becomes your long-term security partner—tuning protections, rolling updates, and standing by 24/7. No offshore call centers—just local experts who know your business and have your back.
Services
Enterprise grade security at an SMB price
We chose each component of our stack to provide maximum security impact with minimum complexity for SMB clients. By leveraging best-in-class open-source tools alongside an integrated platform built for SMBs and smart asset management, we deliver a robust security shield without costly bloat or needless complexity. You get the same caliber of protection used by enterprises and nation-state defenders, fine-tuned for a small business budget and environment.
What makes SIXCYBER unique is our mentoring model. Every client is paired with an expert cybersecurity engineer and an apprentice who grows alongside your company under the guidance of a recognized industry leader. This approach delivers top-tier defense and rapid response while investing in Kansas City’s local talent.
All-in-One Security Platform
Our AI-driven cybersecurity platform is built exclusively for SMBs. This single dashboard allows us to monitor your email system, endpoints, cloud apps, and users. From blocking phishing emails to stopping malware on laptops, our solution provides enterprise-grade protection.
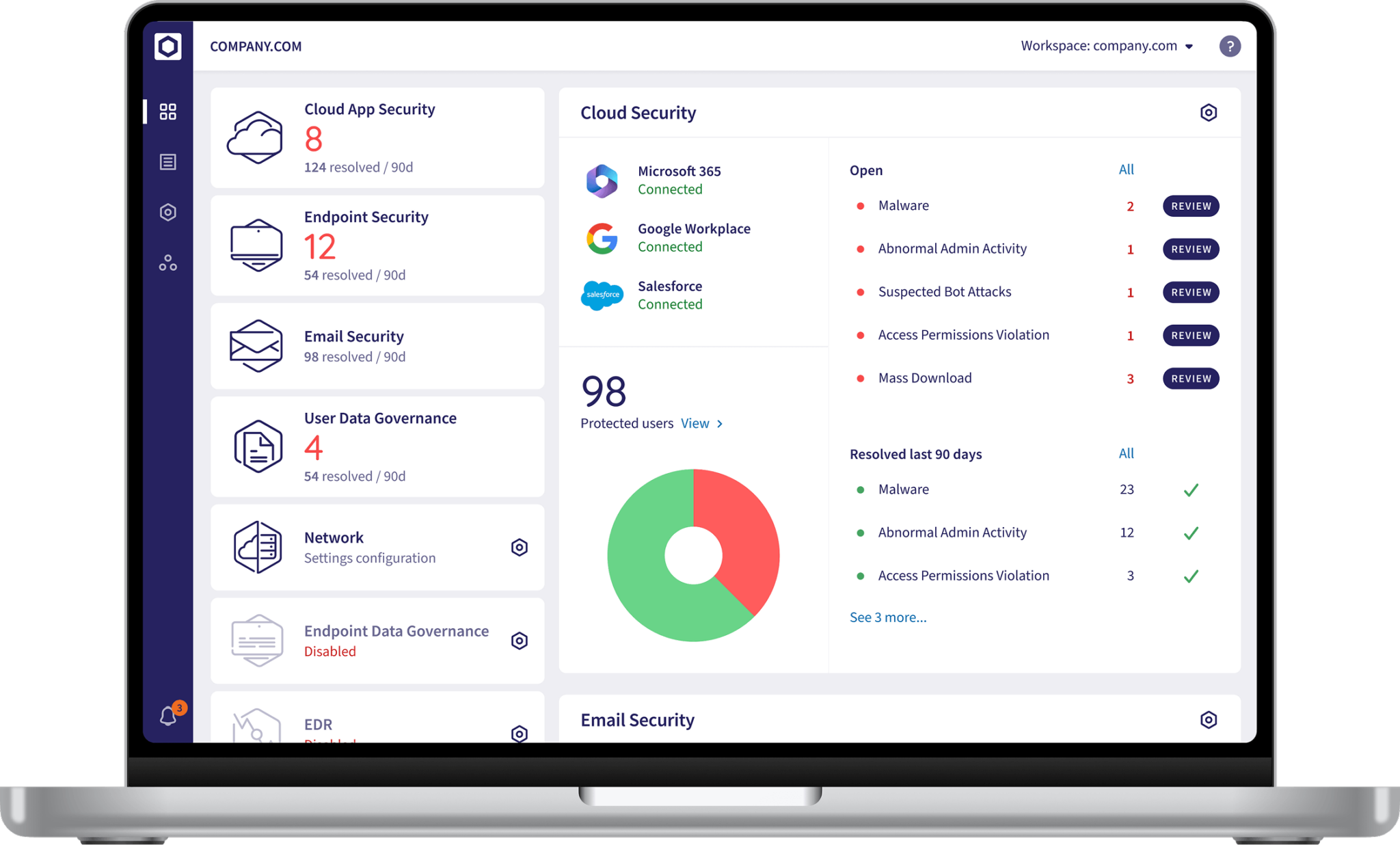
- Most IT providers treat cybersecurity as an afterthought which leaves gaps attackers exploit. Our unified platform makes sure every threat is visible
- Disparate point tools create blind spots. A single dashboard lets us spot phishing, malware and cloud-app threats in one place instead of juggling alerts
- Manual threat analysis is slow and error prone. AI-driven automation identifies and blocks attacks in real time before they impact your revenue
- Juggling multiple vendors drives up cost and management overhead. Consolidating services under one solution simplifies your IT and cuts expenses
- SMBs are increasingly targeted because of weak defenses. Enterprise-grade protection built for small business stops you from being the easiest target
Vulnerability Scanning
We run daily scans of your websites and network looking for vulnerabilities. These continuous “hacker-style” scans proactively find and alert us to any weaknesses in your internet-facing systems – like open ports, unpatched software, or misconfigurations – before attackers can exploit them. By catching issues early, we help you fix them fast and stay one step ahead of threats.
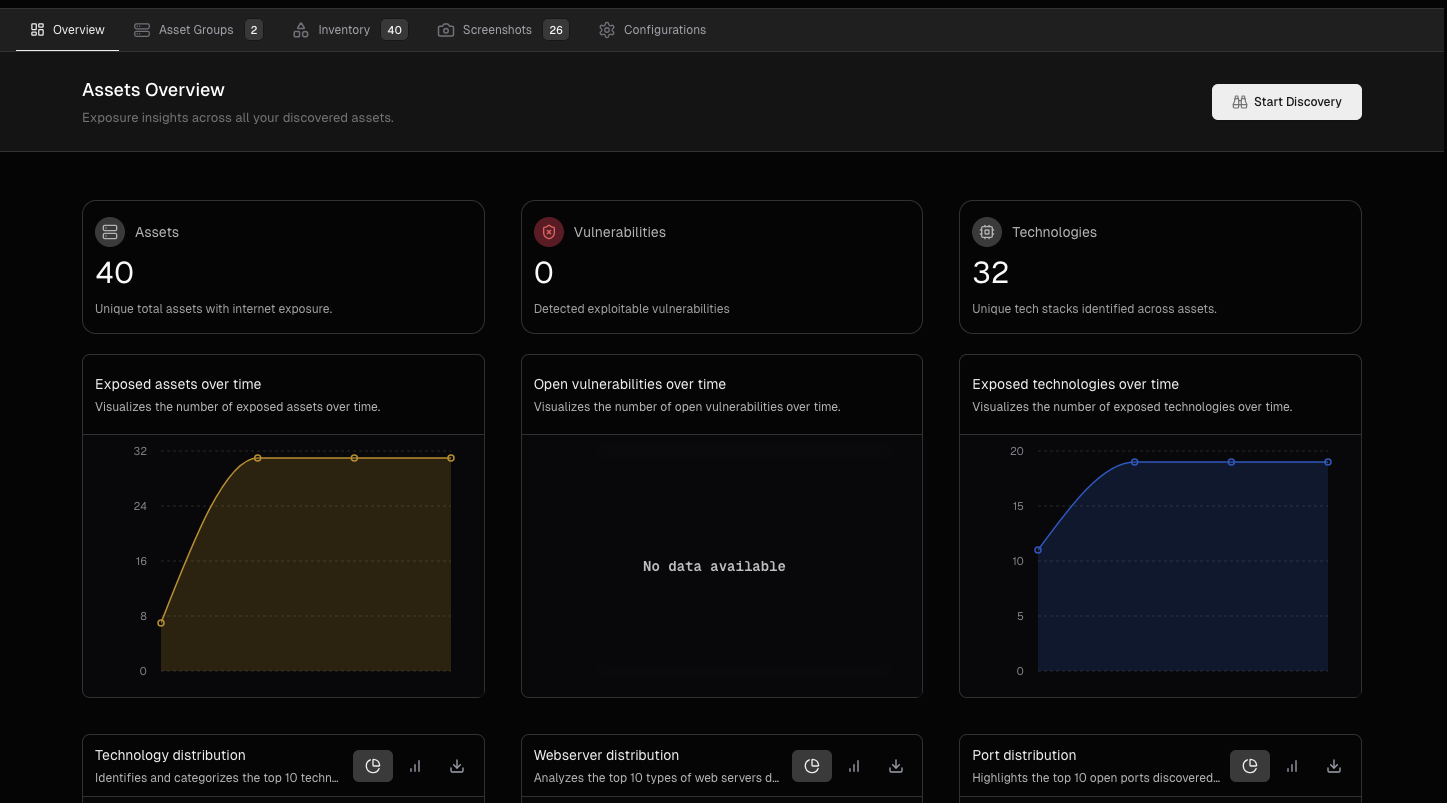
- Misconfigured ports and outdated software are low-hanging fruit; we flag them before criminals exploit them
- Hackers probe internet-facing assets daily; continuous hacker-style scans catch new vulnerabilities instantly
- Routine daily checks uncover gaps like open RDP ports or unpatched VPN software often missed by IT providers
- Finding issues early means less downtime, lower costs and better customer trust
Asset Inventory
You can’t secure what you don’t know about. We use a powerful asset discovery tool that finds every device on your network – PCs, servers, phones, even that forgotten Wi-Fi printer – and keeps an up-to-date inventory. This ensures no device or hidden subnet slips through the cracks.
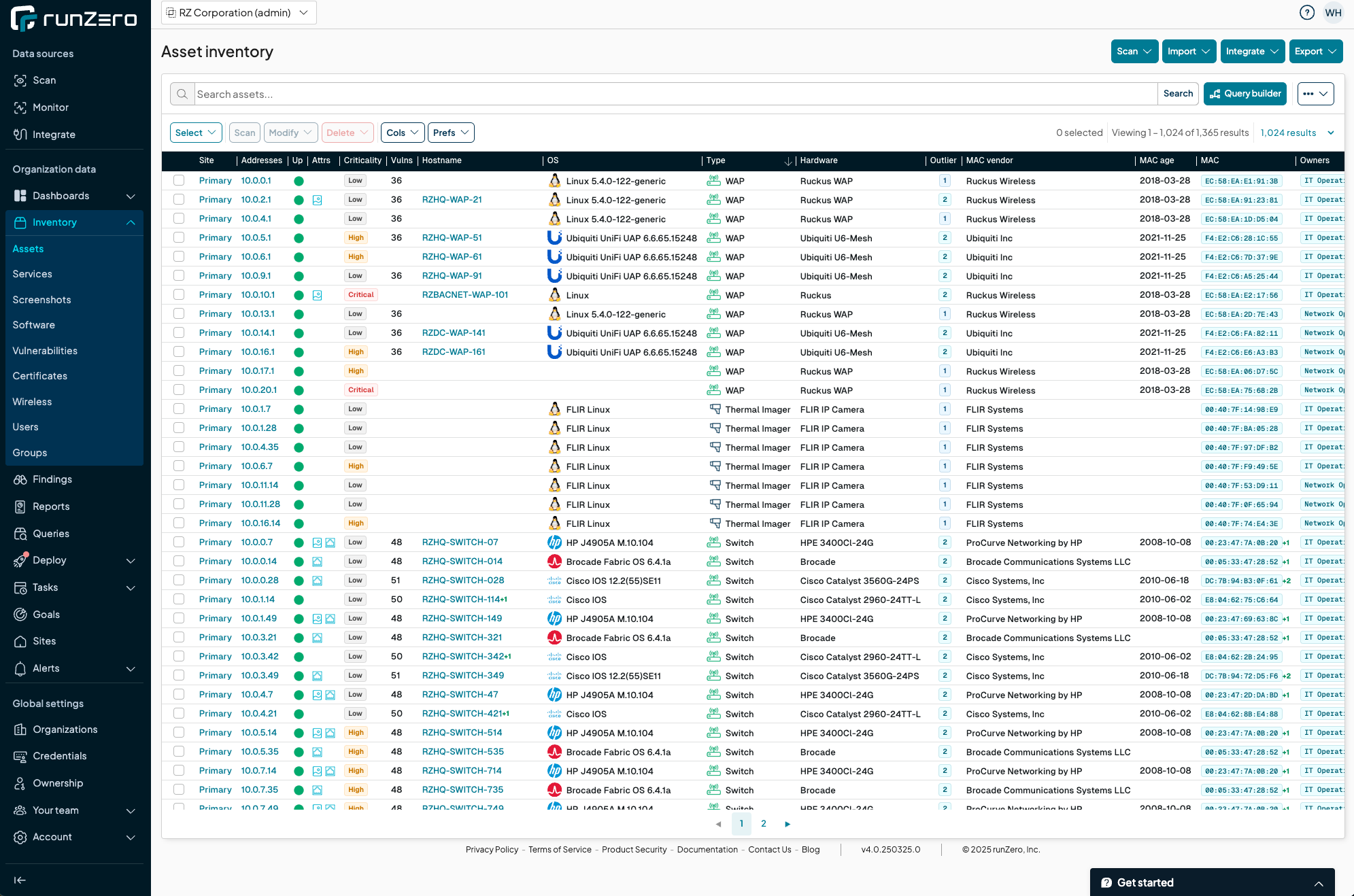
- Real-time discovery flags new devices the moment they appear so you can secure them before they become a problem
- IoT gear, printers and phones often go unpatched and become easy entry points for internal exploits
- Incomplete inventory means your patching and scanning miss critical targets, leaving gaps attackers could leverage
- Spotting internal vulnerabilities early stops attackers from moving laterally and escalating privileges
Adversary Deception
We set up decoy systems inside your network to act as early-warning traps. These fake file servers or services look tempting to hackers, but any interaction with them triggers instant alerts to our team. If an intruder ever gets past the front door, we’ll know immediately when they poke around.

- You get immediate warning of lateral movement before they reach your crown jewels
- Early alerts buy you precious time to contain the breach and limit damage
- Analyzing attacker behavior in the trap helps you shore up real systems more effectively
- Low false positives mean every alert deserves your attention—no chasing ghosts
Pricing
Transparent, easy pricing. Includes every tool, capability and service!
Up to 25 Employees
All-inclusive cybersecurity stack and ongoing monitoring for companies with 25 employees or less
- Advanced Cloud and Endpoint Protection
- Internal and External Vulnerability Monitoring
- 5 Hours of Incident Support included ($200/hr ongoing)
Over 25 Employees
All-inclusive cybersecurity stack and ongoing monitoring for companies with more than 25 employees
- Advanced Cloud and Endpoint Protection
- Internal and External Vulneribity Monitoring
- 5 Hours of Incident Support included ($200/hr ongoing)
CISO on-Demand
Rapid, expert-led breach containment and hands-on CISO leadership for critical events.
- 24/7 emergency incident command
- High-level security strategy & board-room advising
- Collaborate with your existing MSP to review and validate security configurations, ensuring every control is correctly implemented
Contact
Contact Information
Want more information? Lets talk about that.
Email Us
info@sixcyber.com
Schedule a meeting
with Calendly
Send Us a Message
We Want to hear from you!